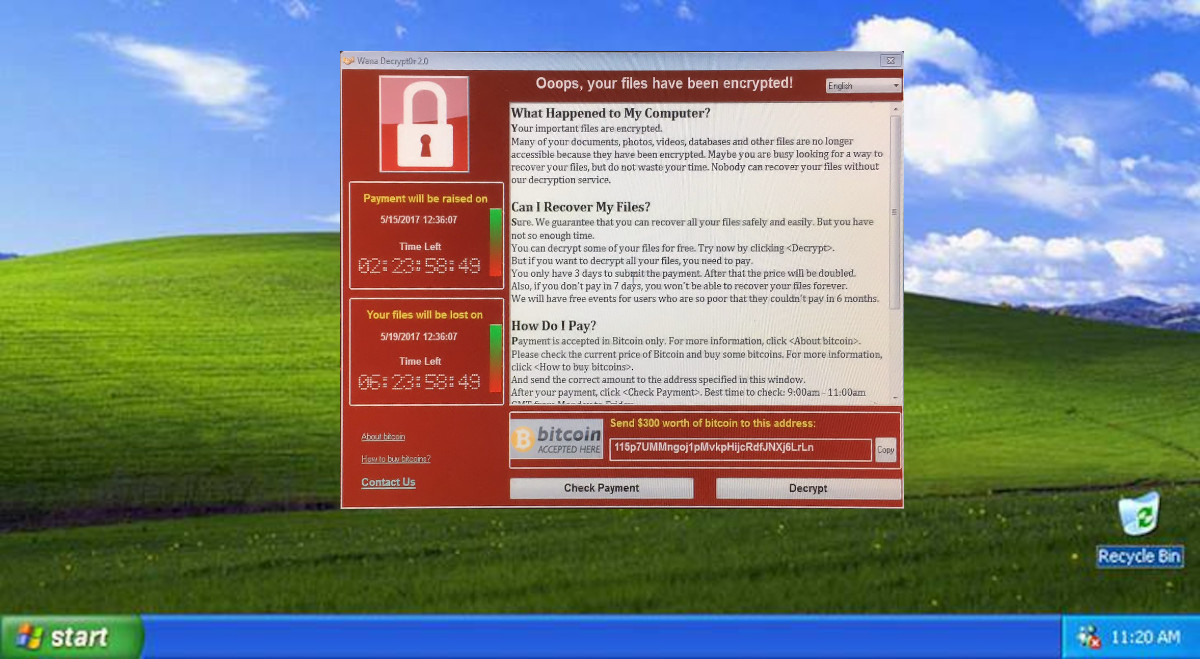
What Is Ransomware?
This form of malware denies the victim access to their files by encrypting them. Then the malware prompts the victim to pay a ransom to recover their data. Most ransomware spreads via email attachments and downloads from malicious websites. Ransomware like WannaCrypt is not a new threat. Ransomware started gaining notoriety back in 2013 with the release of CryptoLocker.
What Makes WannaCrypt So Dangerous?
WannaCrypt is unique in its ability to self-spread. It does not need a user to click a link or download an email attachment. WannaCrypt leverages a Windows SMB exploit nicknamed ‘EternalBlue’. The exploit allows remote hackers to hijack computers running unpatched versions of Windows. Once infected WannaCrypt also scans for other unpatched PCs connected to the network. It also scans random hosts on the wide area network, to spread itself faster.
EternalBlue
EternalBlue is an exploit developed by the U.S. National Security Agency. It takes advantage of vulnerabilities in Microsoft Window’s Server Message Block protocol. Instead of alerting vendors of exploits, governments often stockpile vulnerabilities. This way they can use it for intelligence purposes later. Yet, the Shadow Brokers hacker group found and leaked the SMB vulnerability back in April of 2017.
Microsoft did release a patch in March of 2017 that fixed this exploit. Yet, there remained many critical systems online that never received the patch. System admins often delay patches until testing can prove that it won’t break other services. Also, many of these systems such as Windows XP were out-of-life-cycle. This means they are no longer supported by Microsoft and as such, they did not receive any patches.
The Attack
Friday, May 12 (AKA: Day 0)
The attack hit hard in Europe, infecting over 75k systems in over 99 countries. The attack took some notable victims such as Spain’s Telefonica and Russian MegaFon. The British Nation Health Service had 16 hospitals affected. The hospitals had to turn away patients and cancel scheduled operations. FedEx and the Russian Interior Ministry were also affected by the attack.
Saturday, May 13
A 22-year-old security researcher who calls himself MalwareTech discovered a ‘kill switch’. WannaCrypt would connect to a URL and if it was successful it would continue its attack. The researchers then created a sinkhole by buying the domain and setting it to display a web page. This slowed the infection rate and made it so new infections would not work.
Sunday, May 14
New variants of WannaCrypt get spotted in the wild. Some with new kill-switch domains and others with no kill-switch at all. It’s believed that a third party created the new variants and not the hackers behind the first wave. Yet, it is still unknown who is behind WannaCrypt.
How to Protect Your Systems
Data-Serv Customers
We have already ensured your security against this attack. There is no further action required by you. If you are not a customer and would like to learn more about the services we offer feel free to contact us.
Patch SMB Vulnerability
Microsoft has decided to released patch for its out-of-life-cycle products. You can download the patch for your system on the Microsoft website.
http://www.catalog.update.microsoft.com/search.aspx?q=4012598
Always Install Security Updates
If you are running any version of Windows make sure that you have automatic updates turned on.
Disable SMB
It is advisable to disable the SMBv1 protocol even if you have installed the patches.
- Go to Windows’ Control Panel and open ‘Programs.’
- Open ‘Features’ under Programs and click ‘Turn Windows Features on and off.’
- Now, scroll down to find ‘SMB 1.0/CIFS File Sharing Support’ and uncheck it.
- Then click OK, close the Control Panel and restart the computer.
Block SMB Ports on your Firewall
Always have your firewall enabled. If you need SMBv1 enabled change your firewall config to block SMB ports over the internet.
Use an Antivirus
Use a good antivirus such as Malwarebytes or Trend Micro and keep it up to date.
Be suspicious of Emails, Websites, and Apps
Most ransomware spreads through phishing emails, malicious ads, and third-party apps. You should always exercise caution when opening uninvited documents sent over email. You should never download apps from third-party sources. Also, be sure to read reviews before installing apps from official stores.
Back Up Your Files!
Backups are the best way to defend against this type of attack. Having offsite backups that are not connected to the internet is ideal. If a hacker encrypts your system you can restore your files from your backup and won’t need to pay a ransom.